Customized Health Check Packet – FireEye
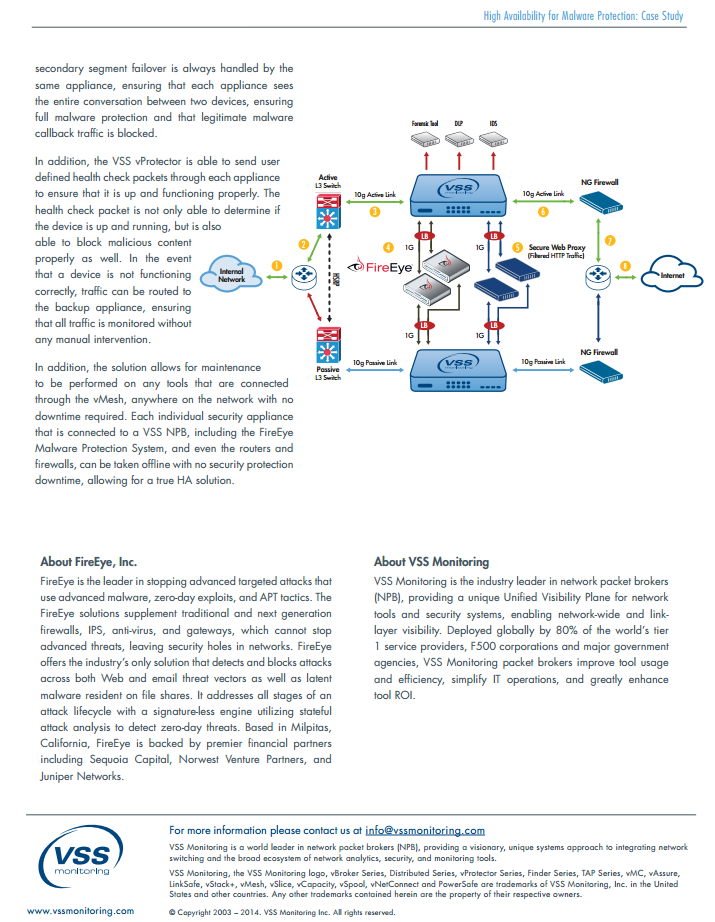
FireEye Health Check Packet

Configuration of FireEye Health Check Triggers with vProtector
FireEye health-check packet format:
FireEye Health Check Packet
NetScout VProtector settings

fireeyecnc.rules:alert udp any any -> [74.86.103.114,92.241.190.252,92.241.190.146,84.19.165.194] 1024: (sid:33332166; rev:1; msg:”503 irc_bot_cmd Bot.Mariposa butterfly_cnc callback-bot block”; dsize:21; content:”|18|”; offset: 0; depth: 1; priority:90;)
45 00 00 2E 00 00 40 00 40 11 6D 09 4A 56 67 72 5C F1 BE FC 00 04 04 00 00 1D 2D FD 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
This packet will check the application stack of FireEye device. Packet will be sent from one connected bridge port to other. If the packet doesn’t receive on other end after certain number of attempt which can be configured in VSS trigger Policy then it will be considered as failure.
__________________________________________
FROM FIREEYE DEVELOPMENT
“We (FireEye) intentionally created the packet to mimic Mariposa call backs, but it does not have the entire content to actually trigger alerts/notifications. The goal was to craft a packet that will allow us to detect potential half hung states, where the MPS is not bridging traffic or is not failing open correctly. The packet will go thru parts of phase1 inspection and should the MPS be in an unexpected state, the packet will not flow thru. We (FireEye) feel this is a better approach than using ICMP or other packets that cannot check bridge status.”
VSS-FireEye Joint Case Study.pdf
Details Written by Aaron Janssen Category: Technical Marketing Published: 11 July 2016 Hits: 20281
